What is Apex Zero Trust Software
March 1, 2022 What is Apex Zero Trust Software
in
IT Support ,
Cyber Security
News by Daniel Shone
Zero trust means changing the position from blocking only known threats to blocking anything from running that is not permitted. When trust is given, granular policy controls are enforced to stop vulnerable applications from carrying out malicious behaviour.
It is primarily Application White Listing Software. It will manage and control at device level, applications, admin control, storage control and provide user activity auditing. Application Control blocks everything from running on your systems that hasn’t been explicitly approved – whether it be a program, an installer, malware or ransomware.
Below is a visual example of why multiple security measures are needed to stop different attack vectors.
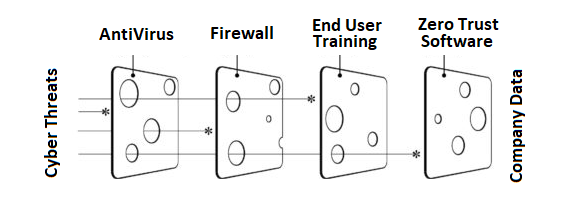
Download our Cybersecurity Threat Report by clicking the image below and find our more about why Zero Trust Software is now an essential part of your security tool kit.
Some Frequently Asked Questions about this Software:
If the user already does not have admin rights to install software, why do we need this?
• You don't need admin rights to run ransomware. You also don't need admin rights to do damage to data. All you need is to be able to run, and access to data. This is why ransomware is so prevalent, and so successful. A ransomware attack, for example could just be a file that only requires opening as opposed to installing, to then encrypt anything which that user had access to. This could run even within the restrictive user account. Threat Locker works the other way and only allows approved applications to run so providing far stronger protection.
Can we provide access to the client or a end user (IT Manager) at a clients to approve software themselves just for their end user devices?
• On request we can do this. It's perfectly suited to this kind of co-managed setup. We only recommend this for IT Managers in the main.
What is the footprint like of your software? Is there a minimum spec device for this to work on? Does it cause performance issues?
• In general it is extremely low impact - it runs between 0 and 1 percent CPU and uses 200 - 600 MB of RAM. It's not like Anti-Virus, scanning files constantly. The agent is sitting there waiting for things to run, and saying yes you can run, or no you can't. It's a binary decision, and one that requires very little computation.
What Devices do you install it on?
• We install it on any Windows based devices that are on, Windows 8, 10 or 11. We also deploy it to supported Server Operating Systems. We don’t install it on Mobile phones or Apple Computers. Although, we will be rolling it out to Apple Computers later in 2022 when the new module is released to support IOS.
Besides Executables, what other types of scripts does it protect against
• Basically anything that can execute - PowerShell scripts, Batch files, VB Scripts, com files, CMD files, msi's & more.
I have Antivirus with Ransomware Protection and a Security Firewall, why do I need this?
• In conjunction with more traditional Anti-Virus and perimeter security (firewalls), we feel a multi layered approach is best to help protect our customers.
How do new Applications get Approved?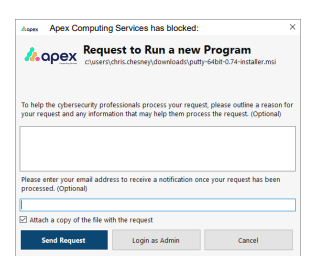
• The approval Center allows Apex Computing Services to easily control what is permitted to run on your computer with a 30-second single click approval. Users have the ability to request permission or ignore notifications for unapproved applications.
Are there other things we should be doing to be more secure?
• There are other Packages and Products which are important for security. We usually discuss these in your Account Reviews, such as, Cyber Essentials Accreditations, Security Audits, Business Grade Firewalls, Staff Training, Phishing Email Testing etc. If you would like to discuss these now please do ask.

